Risk:
Historically, risk managers in organizations didn’t identify, evaluate, and prioritize cyber risks. First, the information security and cyber risks were a national and governmental concern and a later seen as information technology accountability only.
Cyber risk is now a top business risk, and mature organizations manage it with the necessary care, just like any other business risk.
Previous to new industry trends, enterprises didn’t consider boosting their cyber programs as part of their business resilience and being able to adapt is now a key characteristic all organizations need to have.
Cyber-resilience benefits are that organizations can effectively protect data and systems from cyberattacks and resume business operations as quickly and efficiently as possible. Those organizations will have increased overall security and smoother operations. Cyber-resilience will lead to reduced finical losses, enhanced brand reputation, and customer loyalty and reputation.
Identity:
Looking back, we see that Information security managers didn’t see identity on the security radar as identity was an IT and HR accountability. Forward-looking businesses had Identity access management consultants who were helping enterprises implement Identity management solutions to address operational efficiency and automate access provisioning and processes such as joiner, mover, and leaver.
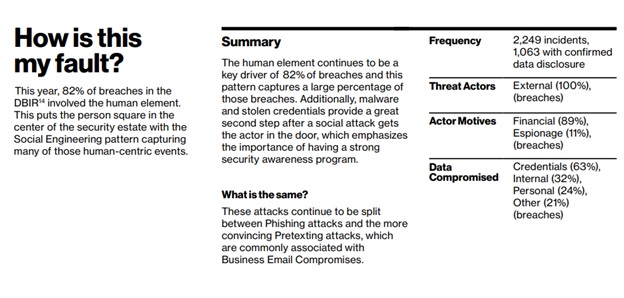
With changing compliance, risk frameworks, and moving organizations to the cloud, identity security is becoming a more and more critical element of cybersecurity and cyber resilience. Enterprises are now accountable for thousands of identities. When identities are not appropriately protected, it is all to easy for threat actors to compromise. The latest 2022 Verizon Data Breach Investigations Report shows that “82% of breaches involved the human element”. Threat actors used compromised identities, usually stolen from a user via (stolen credentials), Phishing, Misuse, Error, etc. Often including privilege escalation.
A recent example of compromised identity is the 2022 Uber data breach. The attacker presided over stolen credentials belonging to an Uber employee purchased from the dark web. Uber’s Privileged Access Management (PAM) platform was compromised through the threat actors elevating their credentials by exploiting users and gaining access to the admin credentials.
The best cyber-resilient organizations see identity security as cyber and business risks and take particular care of those risks. Reducing the identity risk will limit the attack surface of the organization’s environment and reduce the available attack surface and the risk of credential threat.
Current:
Nowadays, good Identity security consultants will not prescribe the best identity solution in the market like it is “one size fits all.” They will first diagnose and assess the organization’s identity security maturity, needs, and risk. The Identity security consultants will guide organizations to set up identity security governance to remediate related risks and comply with the regulations. Then they will prescribe the identity security program – a solution tailored to the organization’s needs, reduce the identity risk to an acceptable level, and boost cyber resilience. These solutions will be aligned with the organization’s Cybersecurity and Strategic objectives.
Building a mature cyberculture is one of the most challenging tasks and will require united agreement with the boards and C-level officers. Leading cyber-resilient organizations’ CEO and board of directors agree on Cyber as a critical risk and driver of an influential and resilient cybersecurity culture tailored to the organization’s mission, vision, and objectives.