Growing Shadows of Ransomware
Contributed by WCF member Eric Gray
It’s hard to open the news and not see the impacts of ransomware on critical infrastructure, food manufacturing, and everything in between. Ransomware has been in development in the cybercriminal world as they drive ways to increase monetization and automate the distribution to impact the highest number of victims. Ransomware originated in the late 80’s initially attacking health care and has exponentially grown (and still attacks health care). In today’s world Phishing is the primary avenue that is used to inject malicious executables and payments average in the millions per incident. Where the money goes is a huge challenge as while bitcoin (most common payment method) has a detailed register its users and account owners is where the darkness lies and money could be directly supporting additional cyber-crime and terrorism.
Let’s cover some of the basics of ransomware and dive into one of the most recent events and a sample negotiation discussion.
Ransomware:
Ransomware is a type of malware that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid. It encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them.
Ransomware attacks are typically carried out using a Trojan disguised as a legitimate file that the user is tricked into downloading or opening when it arrives as an email attachment. However, one high-profile example, the WannaCry worm, traveled automatically between computers without user interaction.
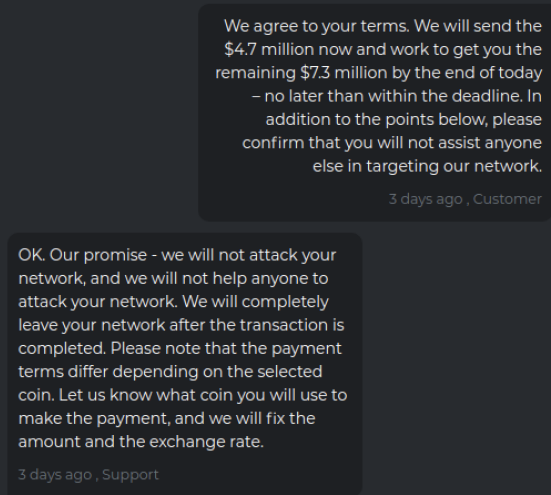
Kill Chain
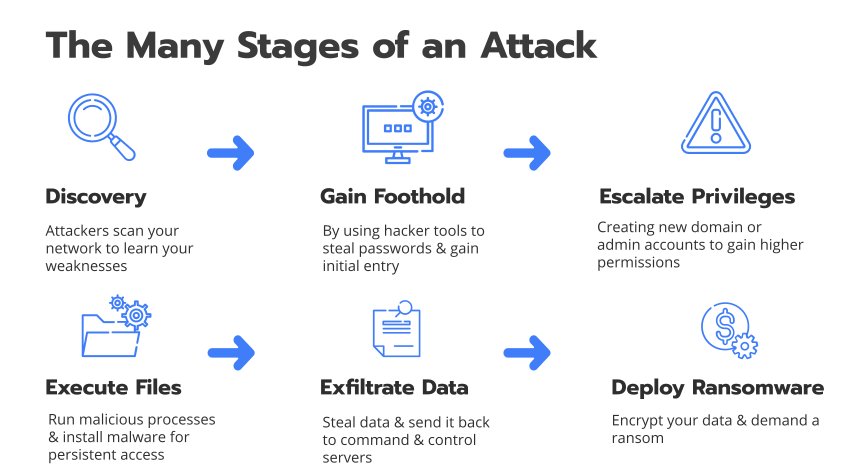
Additional considerations
Payments to ransomware groups are becoming more and more scrutinized by regulators and legal authorities as payments are potentially funding terrorism. Organizations who pay ransomware could be hit with sanctions and fines, as well as be impacted with the other business and organizations that they deal with depending on their moral and culture.
Ransomware Attack Facts:
- 91% of all attacks start with phishing emails
- $3.92 Million was the average cost of a data breach in 2019.
- Hackers attack every 39 seconds and on average 2,244 times a day globally
- Double Extortion: Malicious actors maximize their chance of making profit by giving their victims an additional incentive to pay the ransom – the threat to sell /expose their data.
- New business models are in early stages, when malicious actors have a foothold in a publicly traded company they will short the stock (bet against a stock in hopes it loses value) before they announce publically they have breached or encrypted the data in a company.
Colonial Pipeline Event
Description
On May 08, 2021, Colonial Pipeline reported a ransomware attack and in an effort to contain the ransomware shut down their Operational Technology network, impacting pipeline operations. On May 10, 2021, the FBI attributed the ransomware attack to the Big Game Hunting (BGH) ransomware family, DarkSide. Details of the attack, including the infection vector remain unclear. The attack has impacted the delivery of fuel along Colonial Pipeline’s 5,500 mile network along the US East Coast. The US Government has instituted emergency waivers for fuel transportation regulations in an effort to mitigate potential supply issues.
Analyst Comments
DarkSide ransomware is a BGH Ransomware-as-a-Service (RaaS) operated by the Russian-speaking cybercriminal group tracked as Carbon Spider. Affiliates are known to be recruited from the Russian-language cybercrime community. Available information about the Colonial Pipeline event indicates that the attack was opportunistic, rather than targeted. Also, while the infection vector for this incident remains unclear, it is plausible that any combination of spear phishing emails or malspam containing malicious documents or links, as well as purchasing established network access from vendors within the cybercriminal community were used to gain initial access to Colonial Pipeline’s network.
RaaS (Ransomware as a service) Offering on the darkweb:
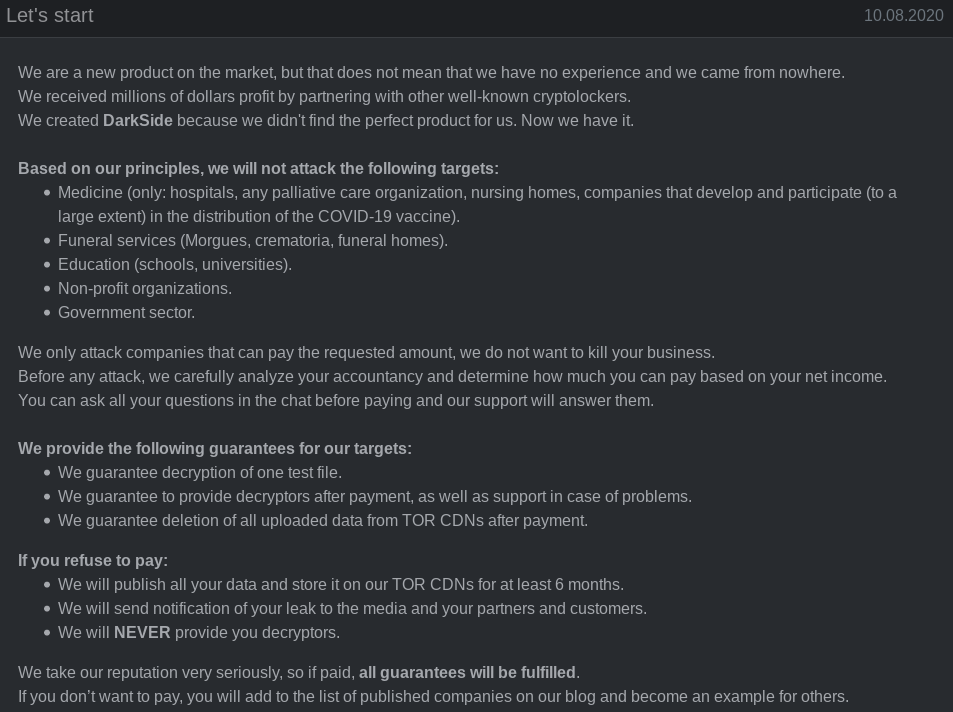
After successful intrusion:
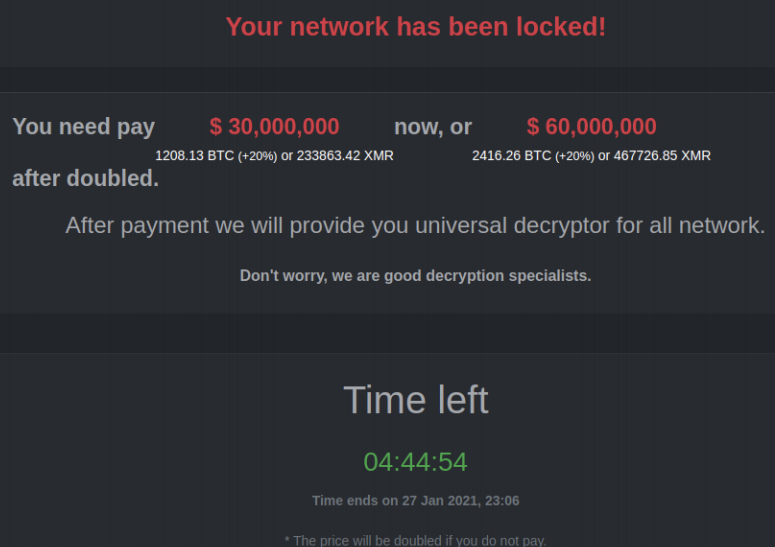
Negotiations:
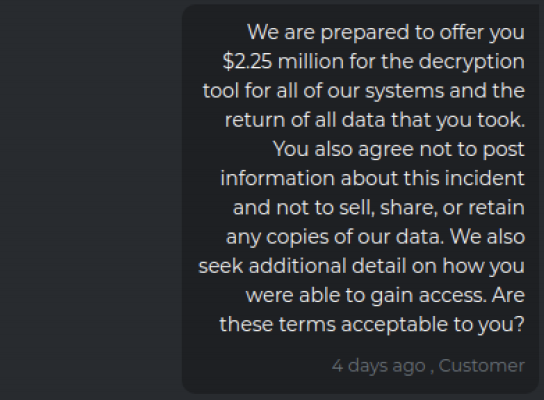
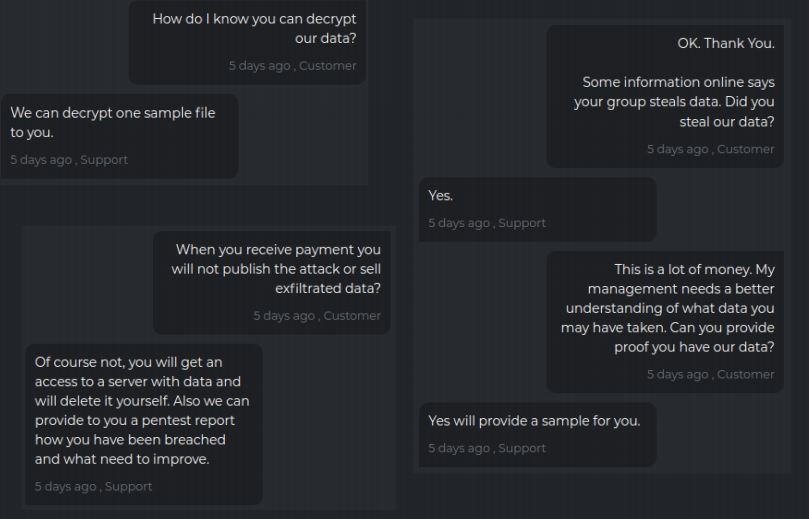
Notice titles, Customer and Support. The malicious actors have created a business model to maximize monetization.
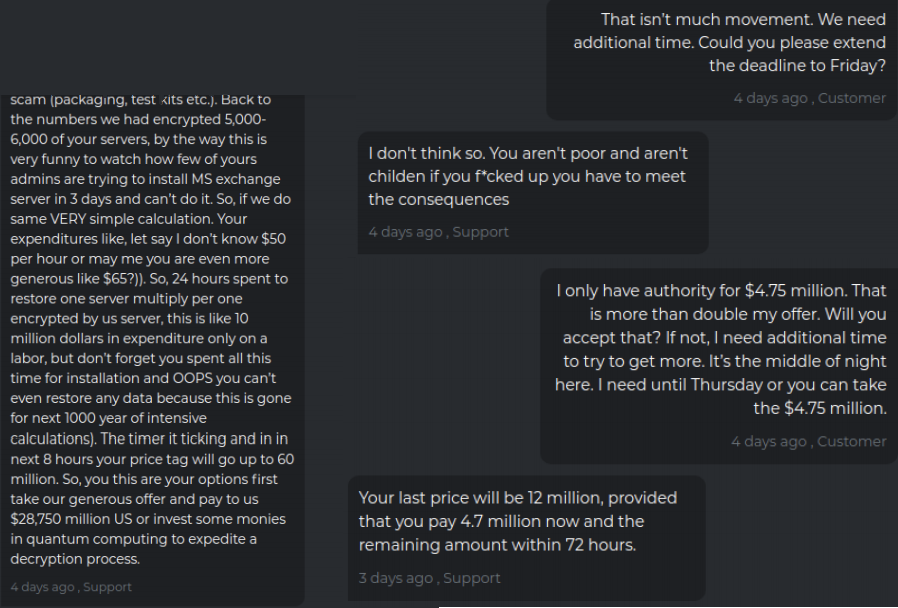
Here the malicious actors break down into dollars, how much it will cost to recover based on standard rates.
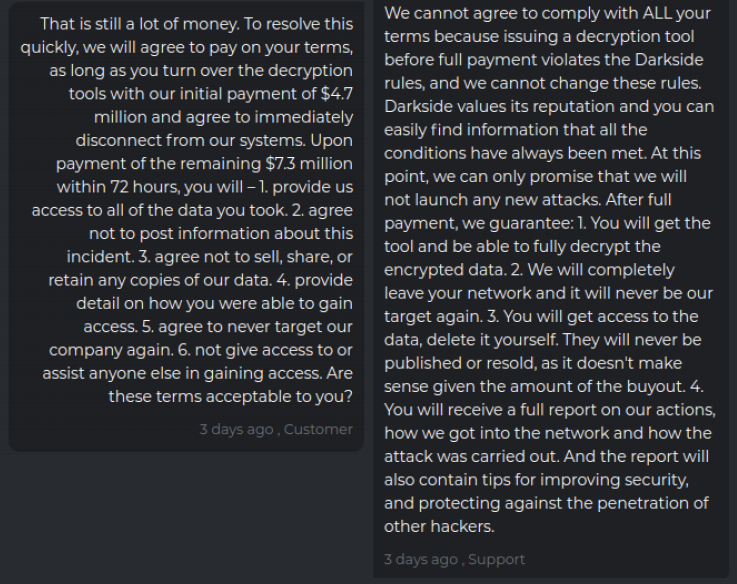
Promises from a criminal organization, are just that.